Mitigating the Risks Introduction Data breaches have become a prevailing threat in today's digital landscape, posing significant risks to...
EU Articles
Breaking News: California Unveils Draft Regulations on CPRA Risk Assessments and Cybersecurity Audits
Introduction In a significant development for data privacy in the United States, the California Data Protection Agency (CDPA) has just...
Unlocking Cyber Insurance Benefits: Data Privacy and Cybersecurity Assurance Frameworks
Introduction In the digital age, where data serves as the lifeblood of business operations, the paramount importance of protecting sensitive...
Balancing Gender Pay Gap Laws and Data Security in Outsourcing
Introduction The quest for gender equality in the workplace has led to the implementation of various laws and regulations to close the gender...
Navigating Compliance: A Guide for U.S. Companies under the New India DPDP Act 2023
Introduction In an era where data is the lifeblood of businesses, the importance of safeguarding personal information cannot be overstated....
A Comparative Analysis: The India DPDP Act v EU GDPR
Introduction Personal data protection has become a significant concern for individuals and organisations in an increasingly data-driven world. As...
The Risk of Delay: Why Waiting for a Federal Data Privacy Law in the USA Can Jeopardise Your Organisation
Introduction In an era of unprecedented data breaches and growing concerns about personal privacy, the absence of a comprehensive federal data...
Ensuring Data Privacy Compliance: Leveraging Independent Privacy Assessments for Data Processors
Introduction Data privacy has taken centre stage in today's data-driven landscape, where personal information has become a valuable asset....
Neglecting 3rd Party Due Diligence Audits: A Costly Gamble with Data Processor Contracts
Introduction The importance of safeguarding sensitive information cannot be overstated in an interconnected digital landscape, where data flows...
The Underestimated Peril: Hackers Targeting Third-Party Data Processors and Data Controllers’ Due Diligence Shortcomings
Introduction In the digital age, data has become an invaluable asset. Consequently, the threat landscape has expanded, with hackers constantly...
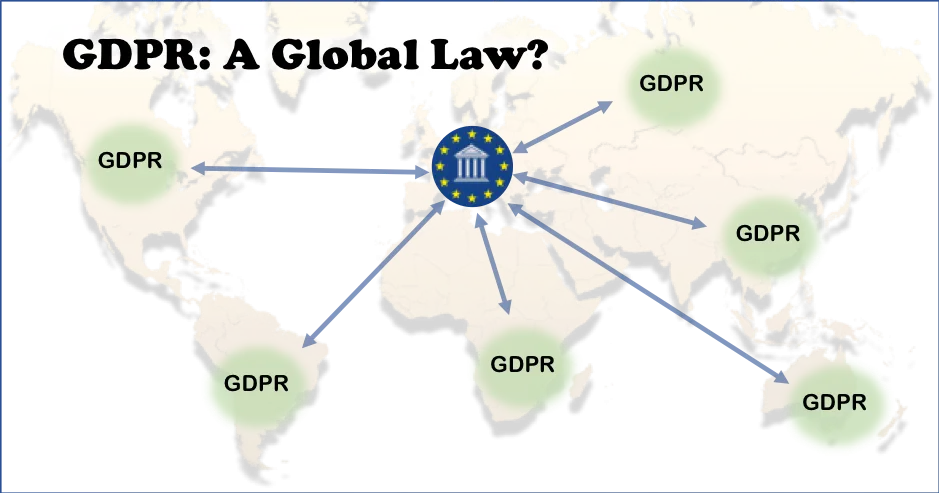
Understanding GDPR Article 3 : Territorial Scope and Its Implications
Introduction The General Data Protection Regulation (GDPR) introduced a groundbreaking framework to safeguard the rights and privacy of individuals...
Building Trust with Legitimate Interest Assessments
The GDPR's Legitimate Interest Assessment: Safeguarding Data Controllers and Processors from Costly Pitfalls The General Data Protection Regulation...