Under the Thailand (PDPA) in Thailand, PDPA controller and processor are required to implement technical and organizational measures to ensure the...
EU Articles
How to Carry Out A Data Protection Impact Assessment
Carrying out a Data Protection Impact Assessment (DPIA) is a process that helps Data Controllers and Data Processors identify, mitigate and minimize...
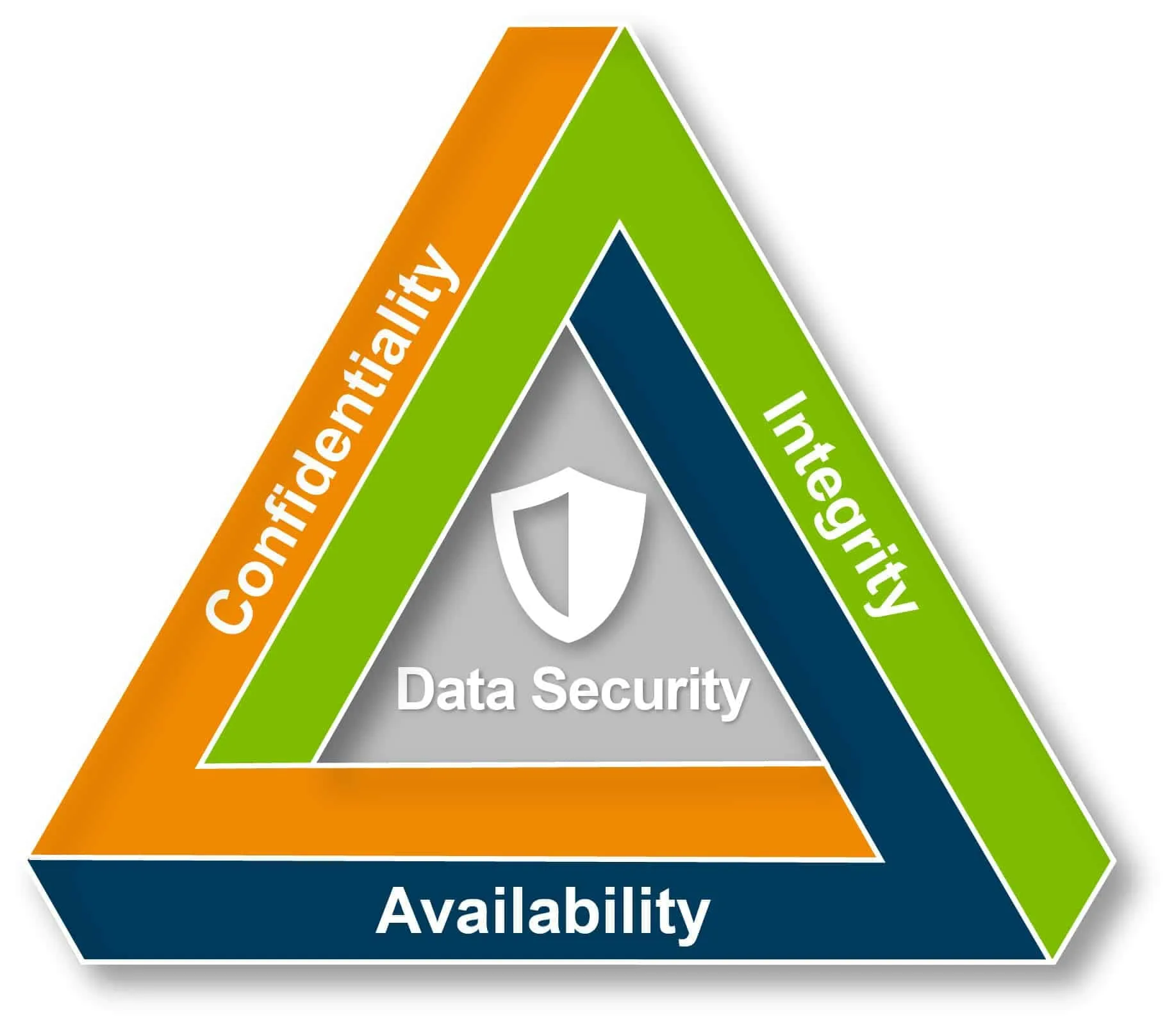
Building Data Breach Protection with A CIA Triad Framework
Introduction: The CIA Triad, which stands for Confidentiality, Integrity, and Availability, is a fundamental concept in information security...
Data Privacy Compliance Management
In our opinion, the future of data privacy compliance management is moving data governance and compliance management into code, a code that fully automates the privacy framework.
GDPR Access Controls: Choosing the Right Model for Your Organisation
It is tempting to give endpoint users administration access to their devices to avoid any complications during the workday. However, this introduces considerable risk to your network because it increases the opportunity for users to compromise personal data.
Yes, Data Privacy Regulations Apply to IOT devices too
Many manufacturers and retailers of IoT devices don’t realise that these devices fall under the purview of data privacy regulations. As data...
GDPR: The Critical Role of Third-Party Due Diligence GDPR
hird-party data breaches pose a significant risk to a company’s reputation. Consider these findings from a survey of 7,500 consumers in France, Germany, Italy, the U.K., and the U.S.:
The Legitimate Interest Assessment LIA: Essential Guide for Data Protection Compliance
An LIA is used to determine if an organisation can process data using the legitimate interest lawful basis. This article explains what lawful bases are under GDPR, and how to complete a legitimate interest assessment (LIA).
Ransomware Attacks The new Big Threat Data Theft
The costs begin to accelerate as the attack progresses. Suppose you are lucky and have cyber protection insurance. In that case, your insurers will need to know the full extent of the breach, often calling expensive third parties to help with the exercise.
GDPR Accountability Principle: A Core Pillar of Compliance
The accountability principle is also in Article 24, which requires controllers to “implement appropriate technical and organisational measures to ensure and to be able to demonstrate that processing is performed in accordance with this Regulation.”
Ensuring GDPR Compliance: Managing Data Subject Access Requests (DSARs)
Introduction In the wake of the General Data Protection Regulation (GDPR), individuals have more control than ever over the personal data companies...
Malaysia (PDPA) Your Guide Part One
Malaysia’s first comprehensive personal data protection legislation, the Personal Data Protection Act 2010 (PDPA), was passed by the Malaysian Parliament on June 2, 2010