Introduction:
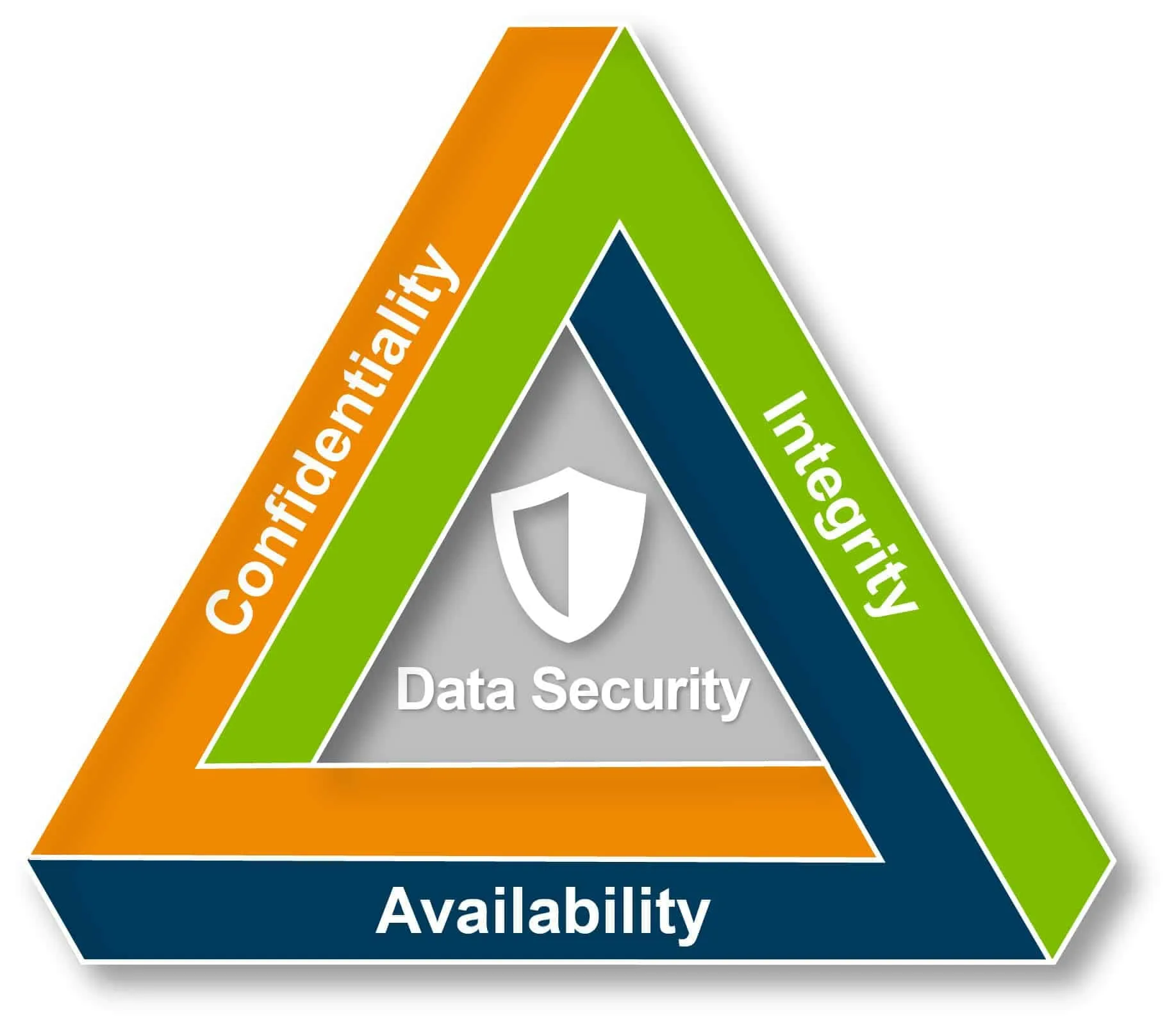
The CIA Triad, which stands for Confidentiality, Integrity, and Availability, is a fundamental concept in information security that describes the three key principles that must be ensured to protect both personal data and sensitive personal data. When one of these principles is compromised, it will almost certainly result in one or more data breaches and security incidents. Hence why organisations should build a data protection with a CIA Triad Framework
A joint study by Stanford University Professor Jeff Hancock and security firm Tessian reported in its findings that 88% of data breach incidents were caused by individual employee errors
Confidentiality:
Confidentiality refers to the protection of sensitive information from unauthorized access. In the context of data breaches, confidentiality breaches occur when an attacker gains access to confidential information, such as financial data or personal information, that they are not authorized to access, or an email recipient receives an attachment in an email which contains the personal data of individuals sent by mistake. These breaches can occur due to weak passwords, phishing attacks, or even physical theft of devices that contain sensitive data. In mosty cases data Breaches are caused by internal mistakes made by employees.
Integrity
Integrity is the principle of ensuring that data is accurate and trustworthy. In the context of data breaches, integrity breaches occur when an attacker manipulates data or changes it in such a way that it becomes unreliable. This can happen when attackers use malware or other techniques to alter data or when they gain access to systems that store data and modify it to their advantage.
Availability
Availability refers to the ability to access information and services when needed. In the context of data breaches, availability breaches occur when attackers prevent users from accessing data or services by causing system outages or denial-of-service attacks. This can happen when attackers flood systems with traffic, use ransomware to encrypt data, or perform other techniques that make systems inaccessible. It can also be caused by organizations who have not invested in redundancy for example two seperate internet connection feeds so if one is comprimised or loses power then the second one can bought into service.
By building your data protection defence on the above three areas ensures you are concentrating on correct areas to avoid one of the three pillars failing. The CIA Triad provides a useful framework for understanding the key principles of information security. Protecting confidentiality, integrity, and availability is critical to preventing data breaches and ensuring that both personal data and sensitive Personal Data is secure. Organizations must be diligent in their efforts to protect their systems and data, implementing robust security measures and continually monitoring for potential threats. By doing so, they can help safeguard their information and prevent potentially catastrophic security incidents that will badly affect the organisations brand.,data