Introduction Recently, the online gaming industry has experienced tremendous growth, with more people than ever before engaging in online gaming...
Hong Kong Articles
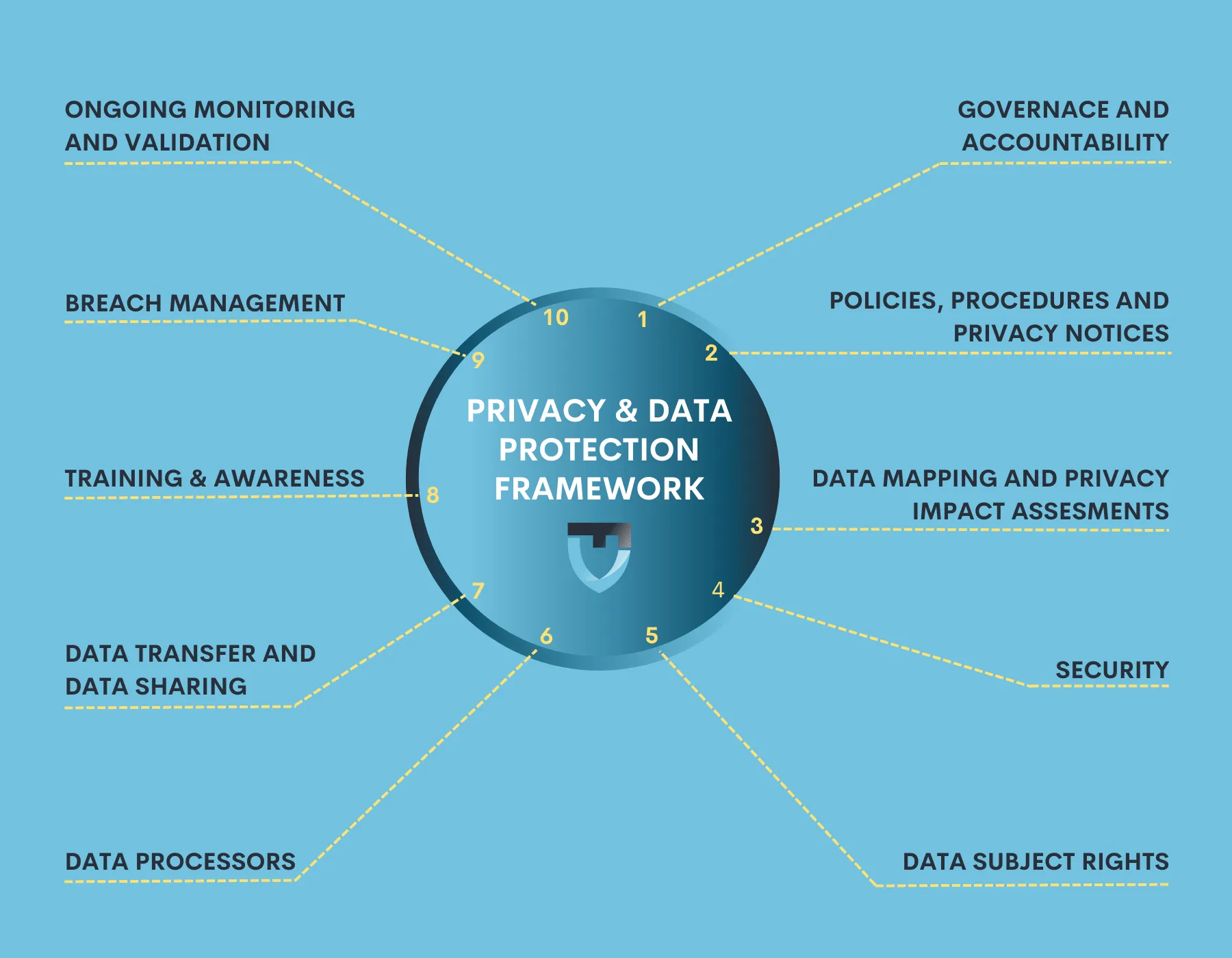
Data Privacy Framework: Essential for Global Privacy Compliance
Organizations must implement appropriate security measures to protect personal and sensitive data from unauthorized access, theft, and other threats. This can include encryption, access controls, and regular data backups. By implementing these measures, organizations can reduce the risk of data breaches and comply with global data protection laws that require organizations to take reasonable measures to protect sensitive data. This can be achieved by strengthening your Technical and Organisational Measures (TOMS) which covers both digital and logical access safeguards.
Why Privacy by Design is Essential for AI Projects
Privacy by design for AI personal data processing is a framework that emphasizes the importance of privacy and data protection throughout the entire...
Why Annual Data Privacy Audits are Essential
Introduction Data privacy has become an essential issue in today's society. The increasing amount of data being collected by organizations means...
Building an Effective and Progressive Privacy Program
Developing an effective Progressive Privacy Program is a complex task that involves numerous stakeholders across various teams, including product...
Not Appointing a UK GDPR Representative Consequences
Under the UK General Data Protection Regulation (GDPR), non-UK businesses that process the personal data of UK residents must appoint a UK...
How to Carry Out A Data Protection Impact Assessment
Carrying out a Data Protection Impact Assessment (DPIA) is a process that helps Data Controllers and Data Processors identify, mitigate and minimize...
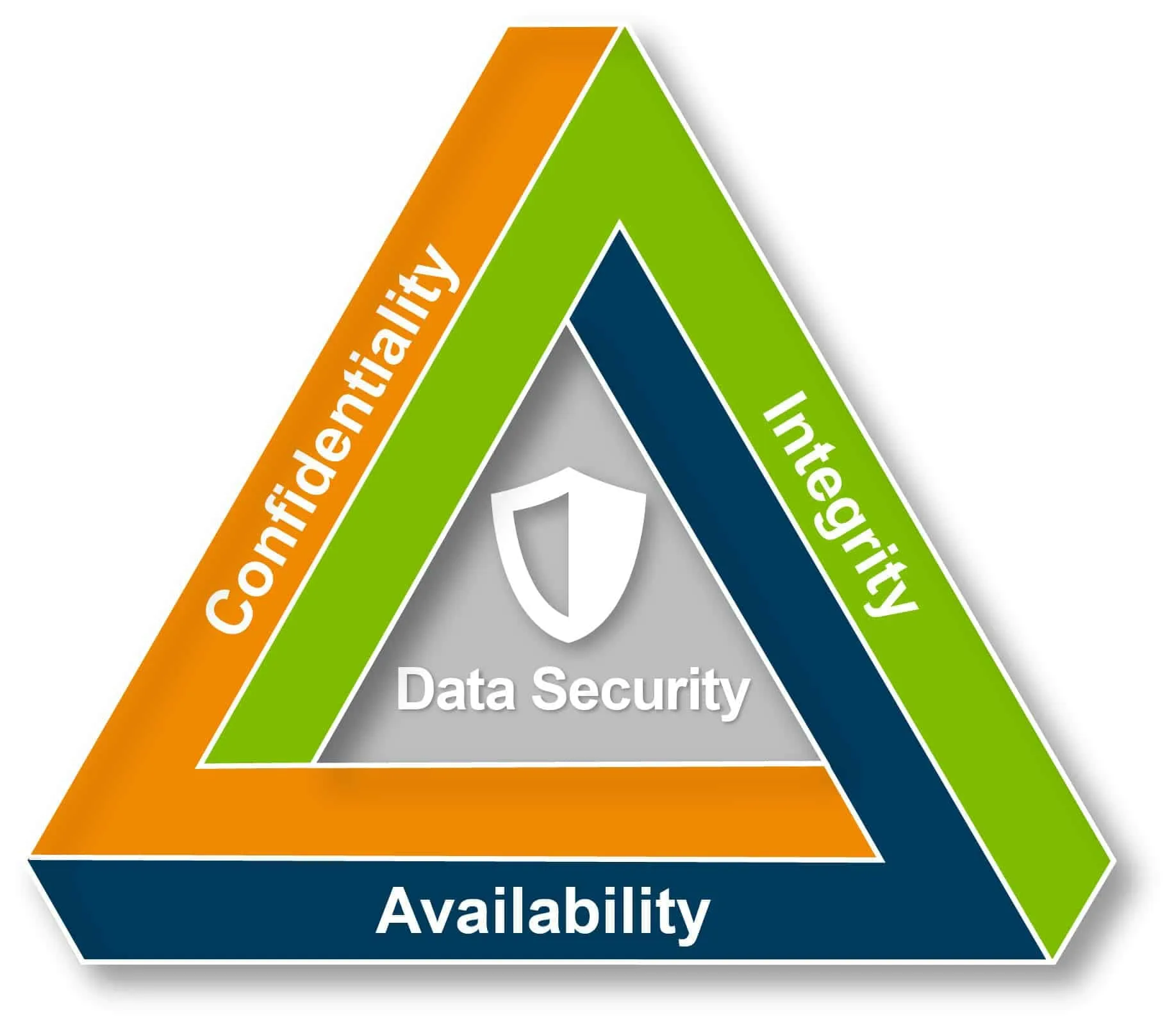
Building Data Breach Protection with A CIA Triad Framework
Introduction: The CIA Triad, which stands for Confidentiality, Integrity, and Availability, is a fundamental concept in information security...
Managing Child and Parental Data in International Schools
Managing child and parental data presents several challenges for international schools. Some of these challenges include: Obtaining and Managing...
How to Complete a Personal Data Breach Report
Not all data breaches need to be reported to the relevant supervisory authority (e.g. the Information Commissioner Office (ICO) in the UK).
Yes, Data Privacy Regulations Apply to IOT devices too
Many manufacturers and retailers of IoT devices don’t realise that these devices fall under the purview of data privacy regulations. As data...
Ransomware Attacks The new Big Threat Data Theft
The costs begin to accelerate as the attack progresses. Suppose you are lucky and have cyber protection insurance. In that case, your insurers will need to know the full extent of the breach, often calling expensive third parties to help with the exercise.