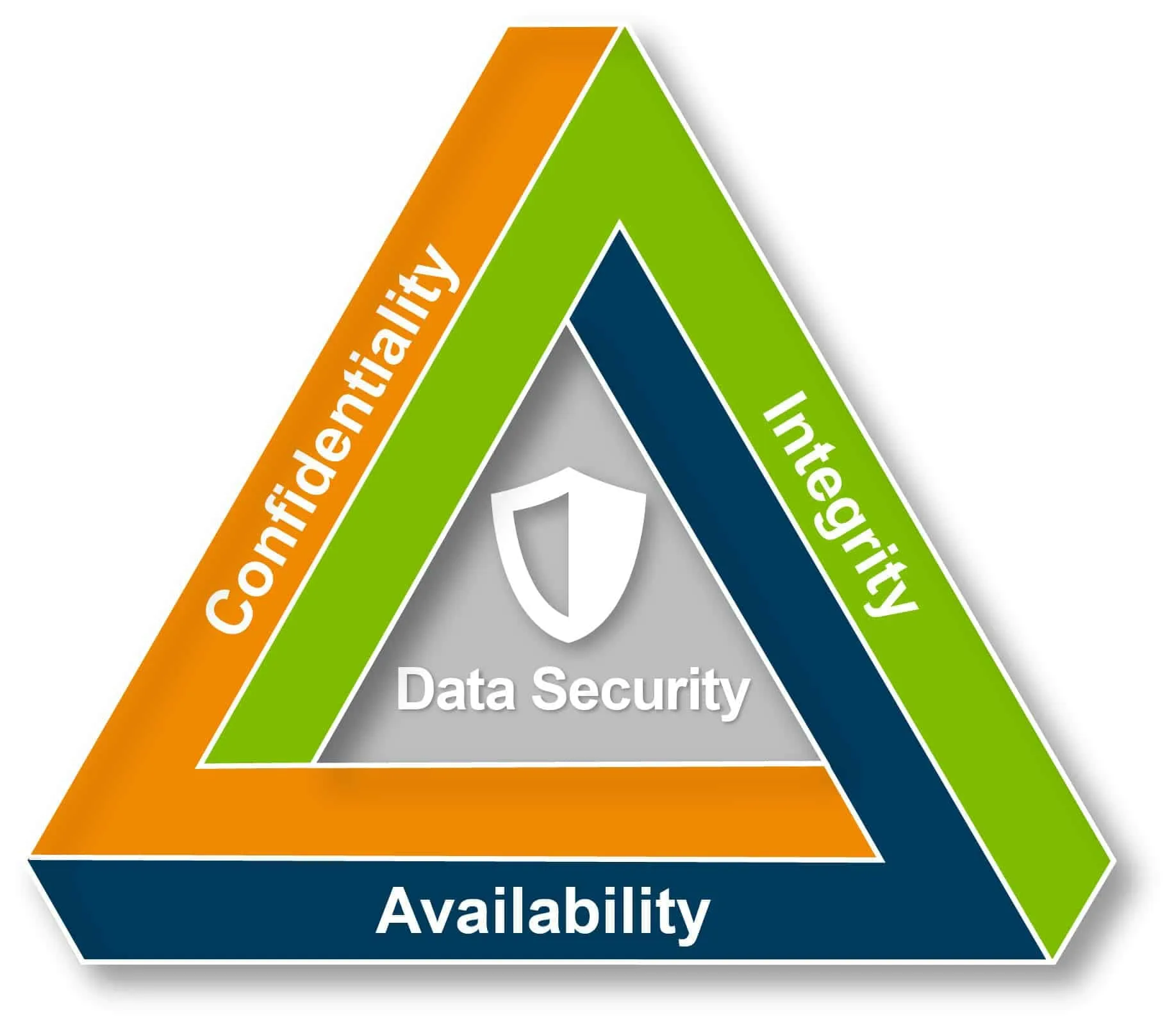
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security. Confidentiality is often associated with secrecy and encryption. Meaning the data is only available to authorized parties. Integrity refers to the certainty that the data is not tampered with or degraded during or after submission Availability, where the information is available to authorized users when needed.
The 3 Pillars of the CIA Triad
There are three fundamental foundations for cybersecurity: prevent data loss, detect data loss and respond to data loss. Most organizations take this to mean prevention. This is paramount. How we protect our data and information will determine how long we have it, who we can share it with, how we can find out if we’ve lost it and how well we can recover it. When we focus on prevention, we get a handle on what is involved. As an information security professional, I often hear complaints that an organization doesn’t focus enough on prevention. Perhaps you are frustrated with the challenges of prevention. There are some steps you can take today to help improve the effectiveness of your defences.
Breach Prevention
By addressing confidentiality, integrity and availability, we can significantly reduce the risk associated with a cyber-attack. Most breaches do not come from malicious individuals but rather from a malicious insider. A breach occurs when users either accidentally expose sensitive information or, more likely, unintentionally give away access. The ability to remediate the initial breach is often a large part of the success of an investigation of a breach. Therefore, it is essential to know what type of information you are dealing with. When we turn to the CIS Benchmark Survey, we find that 71% of IT professionals reported having lost confidential data in the last year.
Protecting Data
The environment within which these systems operate must be clearly defined, securely maintained, monitored, and analyzed to detect and remedy breaches properly. Information security cannot be complete without the organization’s operational processes and procedures aligned with business needs and strategies. Enterprises often allocate as little as 25-35% of resources to information security.
Risk Assessment and Measurement
Risk assessment is the process of identifying the impact an event could have on an organization’s assets. The more an organization understands the cost of breaches to business operations and data, the more likely it will mitigate that impact. Understanding the cost of a breach can be difficult, but the good news is that organizations have the tools to quantify it. Some organizations take a proactive approach by creating a detailed list of what could go wrong. This process is called a risk assessment. The comprehensive nature of risk assessments allows them to provide a risk score for every component of the triad and the tools that support the CIA triad. The Formiti Pontus partnership is introducing an open-source software-based solution FormitiX due for release in September 2021
Conclusion
Information security is essential for business success. Taking these basic components into consideration in developing your data protection strategy is a step in the right direction. Keep up with the latest data security tips and best practices with the Formiti newsletter. Subscribe.
Did you know? Thirty-seven per cent of all compromised companies are ransomware victims. Forty-six per cent of companies affected by a compromise are unaware of the breach, forty-five per cent of enterprises experienced a cyber-attack in the past year, and 32 per cent of information security professionals have a problem with the data and information they hold. How comfortable are you with your cybersecurity and data protection strategy?