Introduction The newly enacted California Privacy Rights Act (CPRA),which went into effect on January 1, 2023, California CPRA Audit Requirements...
EU Articles
How a Data Privacy Champions Group Can Take Your Privacy to the Next Level
Introduction Data privacy has become increasingly important in recent years as more companies collect and process vast amounts of personal data....
The Virginia Privacy Law VCDPA and its obligations for Marketing Teams
Overview of the VCDPA The Virginia Consumer Data Protection Act (VCDPA) is a comprehensive privacy law that was enacted on March 2, 2021, and will...
How Privacy By Design Can Reduce Software Development Time
Introduction Data privacy is an essential aspect of software development. As data breaches become more common, software developers must prioritize...
Online Game Publishers Under Privacy and Online Harms Pressure
Introduction Recently, the online gaming industry has experienced tremendous growth, with more people than ever before engaging in online gaming...
Data Privacy Framework: Essential for Global Privacy Compliance
Organizations must implement appropriate security measures to protect personal and sensitive data from unauthorized access, theft, and other threats. This can include encryption, access controls, and regular data backups. By implementing these measures, organizations can reduce the risk of data breaches and comply with global data protection laws that require organizations to take reasonable measures to protect sensitive data. This can be achieved by strengthening your Technical and Organisational Measures (TOMS) which covers both digital and logical access safeguards.
Why Privacy by Design is Essential for AI Projects
Privacy by design for AI personal data processing is a framework that emphasizes the importance of privacy and data protection throughout the entire...
Six Steps For UK Online Harms Bill Compliance
The UK government's Online Harms Bill aims to regulate online platforms and make the internet a safer place for users, particularly children. The...
Why Annual Data Privacy Audits are Essential
Introduction Data privacy has become an essential issue in today's society. The increasing amount of data being collected by organizations means...
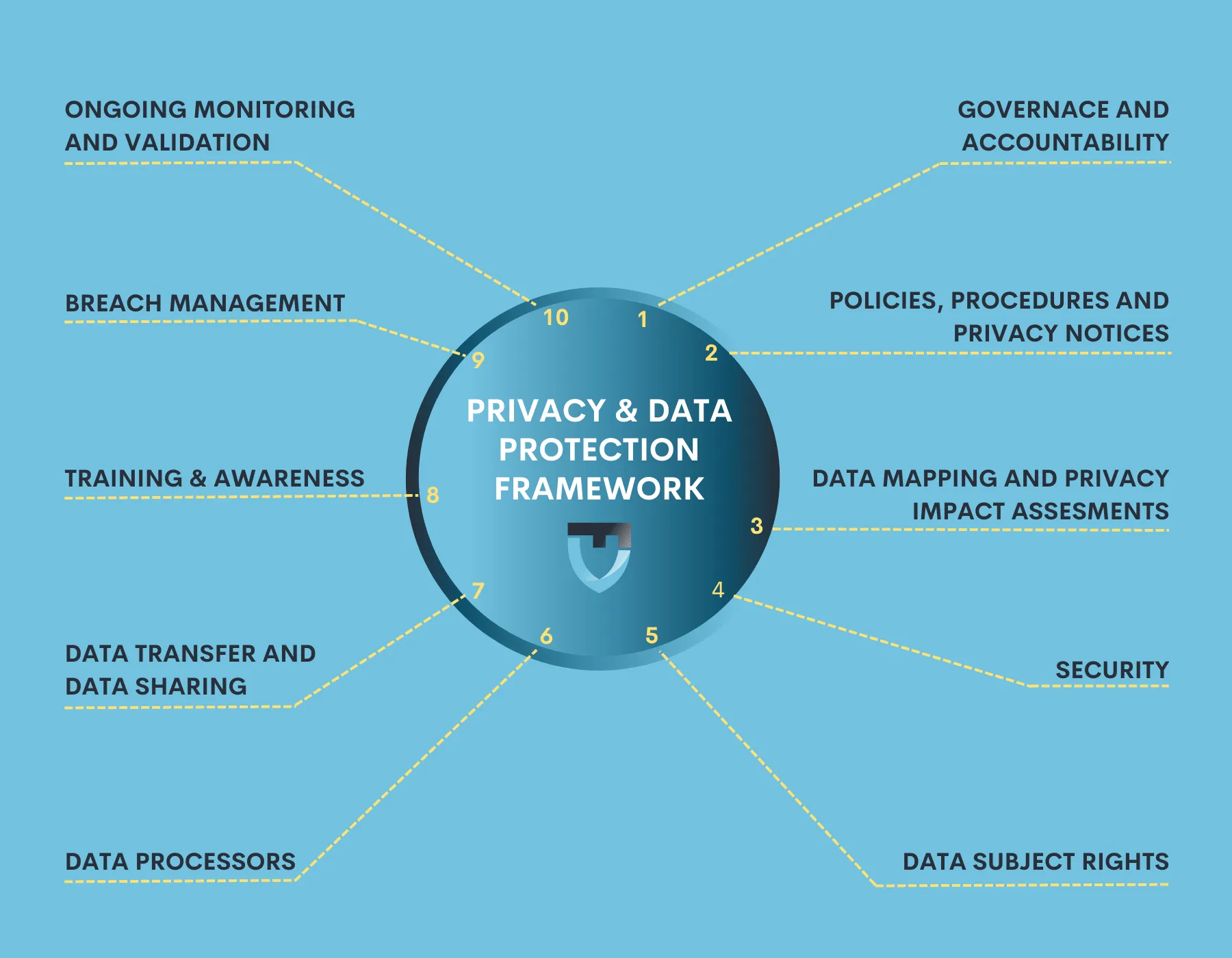
Building an Effective and Progressive Privacy Program
Developing an effective Progressive Privacy Program is a complex task that involves numerous stakeholders across various teams, including product...
Five Steps For Essential Privacy Compliance for HR
Post Covid flexible working and international recruitment has grown exponentially. Alongside this trend is the rapid enactment of global data...
Big Tech and Privacy Contract Clauses. Stand Your Ground
At some point, organisations worldwide have encountered the classic Cooperation Clause or one similar. Many organisations fail to pick up on Privacy...