Introduction As Artificial Intelligence (AI) becomes more widespread, comprehending its legal framework is crucial, especially concerning the and...
Philippines Articles
Safeguarding Your Business: The Crucial Role of a UK GDPR Representative
Introduction: The Vital Need for a UK GDPR Representative For non-UK organisations involved in processing the personal data of UK residents, the...
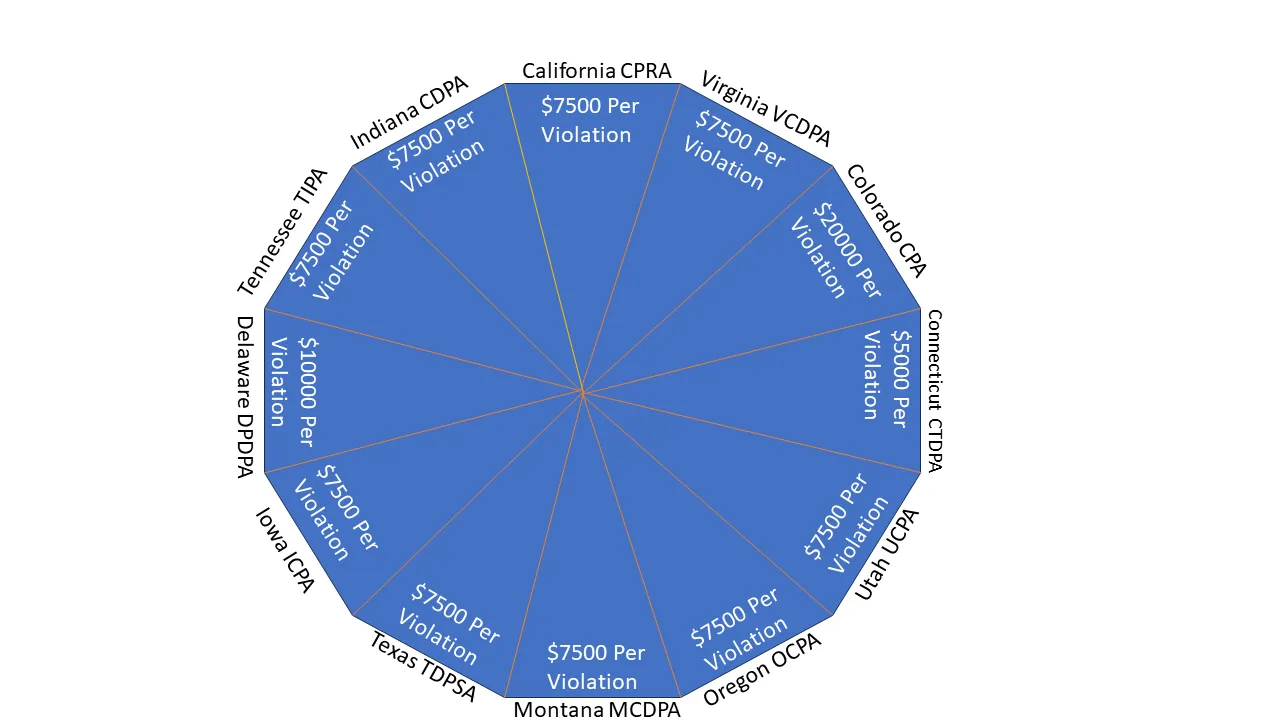
Adapting to US State Privacy Laws: Challenges for Global Organisations
Introduction In an era where data is as valuable as gold, the United States presents a unique challenge for global organisations: a patchwork of...
Navigating the AI Maze: Bridging the AI Regulatory Maze
Introduction In today’s digital epoch, artificial intelligence (AI) stands at the forefront of innovation, reshaping industries and revolutionising...
Charting the Course for Ethical AI: The Emergence of AI Ethics Officers
Introduction In an age where Artificial Intelligence (AI) is becoming deeply integrated into our daily lives and business operations, the focus on...
Navigating the Labyrinth of State Privacy Laws: The Elastic Data Privacy Framework Solution
Introduction In an era where digital information flows like a ceaseless torrent, businesses grapple with an increasingly intricate tapestry of state...
Navigating the New EU AI Draft Act: Essential Insights for Data Privacy Professionals
Introduction The evolving framework of Artificial Intelligence (AI) regulation within the European Union is crystallizing with the advent of the new...
Thailand PDPA Update: DPO Appointment Requirements from 13 December 2023.
Introduction The landscape of data privacy is continuously evolving, and with it, the regulations governing personal data protection. In a...
Preventing Holiday Phishing Attacks in the Workplace: Protecting Your Company’s Data
Introduction As the holiday season approaches, a festive atmosphere envelops the workplace, but it's also a time when threat actors become...
Proposed Changes to Cross-Border Data Transfers Under China’s PIPL
Introduction In a significant development for the global business community, China is set to ease its cross-border data transfer (CBDT) requirements...
Draft Audit Measures Under China’s PIPL: What Businesses Need to Know
Introduction The Personal Information Protection Law (PIPL) in China, a cornerstone of the country's data privacy framework, is set to undergo a...
Top 3 WordPress Vulnerabilities for November 2023: A Deep Dive into Security Risks and Exploits
Introduction WordPress, a powerhouse in the world of content management systems, is known for its flexibility and a vast array of plugins and...