Introduction Data privacy has taken centre stage in today's data-driven landscape, where personal information has become a valuable asset....
Malaysia Articles
Neglecting 3rd Party Due Diligence Audits: A Costly Gamble with Data Processor Contracts
Introduction The importance of safeguarding sensitive information cannot be overstated in an interconnected digital landscape, where data flows...
The Underestimated Peril: Hackers Targeting Third-Party Data Processors and Data Controllers’ Due Diligence Shortcomings
Introduction In the digital age, data has become an invaluable asset. Consequently, the threat landscape has expanded, with hackers constantly...
Building Customer Trust through a Comprehensive Data Retention Policy
Introduction In today's digital age, data breaches have become a serious concern for organisations across various industries. Maintaining customer...
Data Transfer Impact Assessments and How To Execute Them
Introduction In today’s interconnected world, businesses frequently transfer personal data across borders. Each international transfer...
Data Privacy by Design: Building Privacy Into Technology
Prioritizing Privacy in a Data-Driven World Introduction: In today's digital age, where data is the lifeblood of countless technologies and...
California CPRA Audit Requirements
Introduction The newly enacted California Privacy Rights Act (CPRA),which went into effect on January 1, 2023, California CPRA Audit Requirements...
How a Data Privacy Champions Group Can Take Your Privacy to the Next Level
Introduction Data privacy has become increasingly important in recent years as more companies collect and process vast amounts of personal data....
The Virginia Privacy Law VCDPA and its obligations for Marketing Teams
Overview of the VCDPA The Virginia Consumer Data Protection Act (VCDPA) is a comprehensive privacy law that was enacted on March 2, 2021, and will...
How Privacy By Design Can Reduce Software Development Time
Introduction Data privacy is an essential aspect of software development. As data breaches become more common, software developers must prioritize...
Online Game Publishers Under Privacy and Online Harms Pressure
Introduction Recently, the online gaming industry has experienced tremendous growth, with more people than ever before engaging in online gaming...
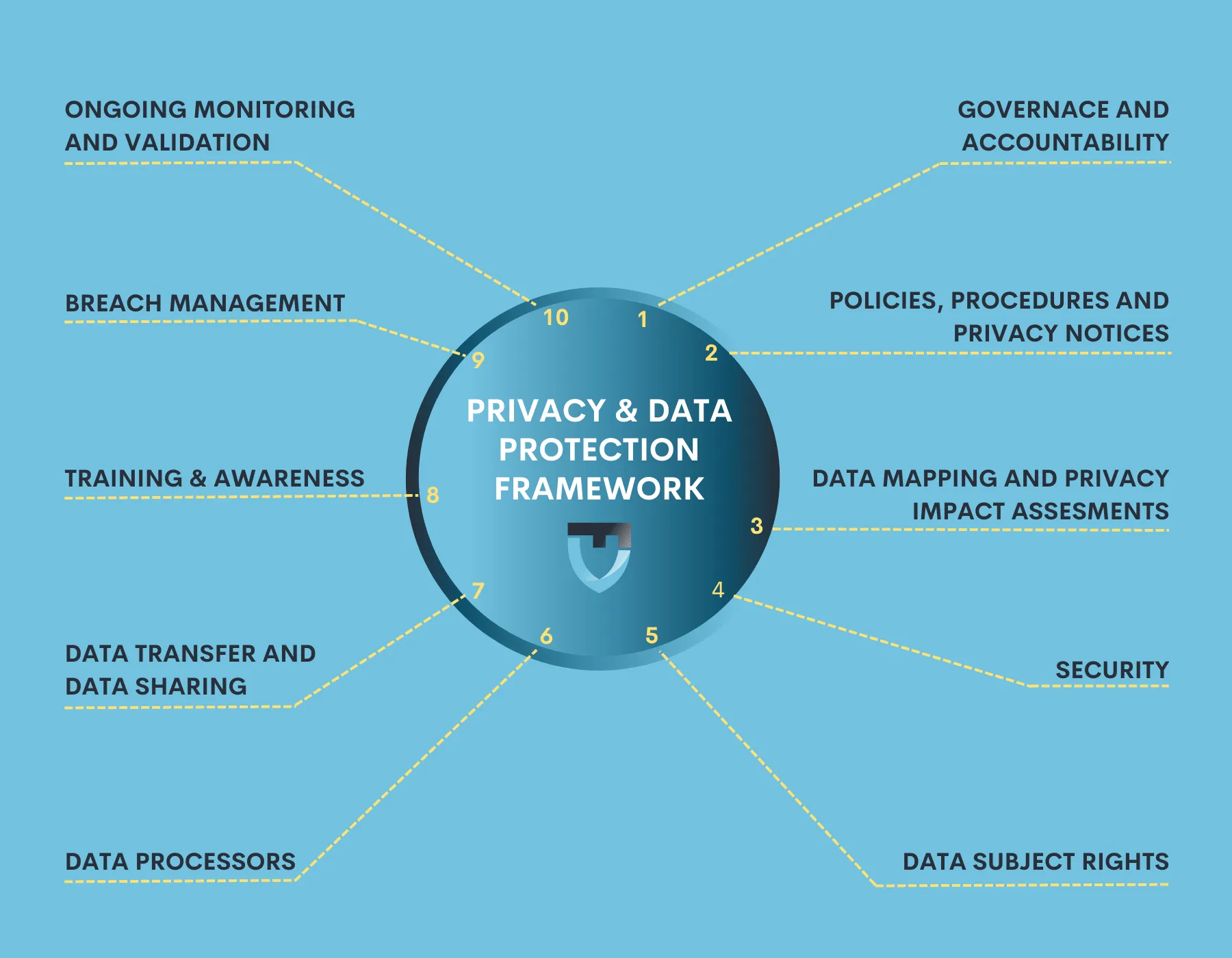
Data Privacy Framework: Essential for Global Privacy Compliance
Organizations must implement appropriate security measures to protect personal and sensitive data from unauthorized access, theft, and other threats. This can include encryption, access controls, and regular data backups. By implementing these measures, organizations can reduce the risk of data breaches and comply with global data protection laws that require organizations to take reasonable measures to protect sensitive data. This can be achieved by strengthening your Technical and Organisational Measures (TOMS) which covers both digital and logical access safeguards.